Update 20180202: I didn't realise this was still coming up in search results, but it's been brought to my attention from a couple of sources that TrueCrypt seems to now be defunct and a lot of the Firefox add-ons now won't work with the most recent versions of Firefox. So please keep this in mind if you're reading this now.
For good results do levels 1 and 2. I highly recommend level 3. 4 is optional extra and 5 if you're extra paranoid. In a section after level 5 I also include some slight modifications to the installation guide for Ubuntu because I believe making the switch to Linux is really worthwhile if you don't need a program (or suite of programs) that doesn't have a Linux version. If you find any of "free", "secure" and "probably ethical" (I think) desirable in an operating system (all at once even!) hit up the Got Linux? section first and then come back to top. It's at the bottom because I was building up from pretty-easy-to-do to requires-a-bit-of-effort.
Note: most of the instructions are MacOSX Lion and Firefox-centric as that's what I use. Firefox is the same across all operating systems. The only difference is the location of their preferences panel; in OSX it's in the Application menu (it's right next to the Apple menu in the top left hand corner and will say "Firefox" when Firefox is in focus) and in Win7 and Ubuntu it's in Edit -> Preferences. Other browsers should have similar settings about the place but you're on your own there :)
Note 2: this is a GUIDE not an instruction set. You do not have to do everything laid out here exactly as stated. You can skip things or modify them to suit your requirements.
Note 3: the guide focuses on privacy and security, NOT anonymity. Privacy in this case means giving information to people you want to give it to and not having anyone else snoop in on it and use it for whatever they want. It may make your browser stand out a bit, which is only a concern if someone is targeting you specifically. The stuff outlined in here will help you avoid trackers and keep some control over where your data is going, but it will not magically make you safe and/or anonymous. You still need to be conscious of what you're doing and why, and you still need to monitor your kids while they're online.
Disclaimer: I'm a hack not an expert, and I'm using/plugging stuff I'm familiar with. You can do your own research. You do not have to trust me. Even if you do trust me, read up a little bit on some of this stuff anyway. Just don't bubble ;)
Update 0000F14x | 2013-05-23: made a collection called Fortifox with most of the extensions used in this guide.
Level 1 - browsing/sharing behaviour
General gadding about
- BE CAREFUL WHAT YOU CLICK ON. Some things that look like legitimate links are actually ads designed like that to trick you into clicking on them. This is less of a problem when you install Adblock Plus in level 2. Some things are virii/malware. ALSO BEWARE OF LINKS POSTED ON FACEBOOK TIMELINES (especially if they have brainless leads like "Is this you?").
- DO NOT OPEN EMAILS OR CLICK LINKS IN EMAILS FROM PEOPLE YOU DON'T KNOW OR FROM PEOPLE THAT YOU DO KNOW IF IT LOOKS OUT OF CHARACTER.
- please forgive bek for screeching blindingly obvious things.
- some sites or things that you download will want you to turn off your antivirus so that it will "work properly". Do not turn off your antivirus. Did I mention do not turn off your antivirus? Well, do not turn off your antivirus.
- Do not activate Google's web history (or any other search engine equivalent). If you have, turn it off, clear it and flush your cookies, caches, history, and stored forms and passwords.
Social networking (Facebook, G+, Twitter, etc)
- don't enter your email address into a site unless you actually want an account at that site. If you're wanting to follow a blog, click the feed icon (they're the usually orange radar thingies like the ones in my Categories block in the right sidebar, some sites change the colour to match their scheme better). Most email clients these days will double as feed readers so you don't need to install anything extra unless you want to.
- user/display names (same for most sites, some will let you have a separate username that you log in with and display name that is shown on your profile/forum posts/etc):
- real name: assuming you don't live in a regime that needs to be overthrown or there isn't someone out there who wants to kill you for some reason, the only really bad thing about using your real name on the internet is if someone with your name has a tendency to share things they shouldn't which may end up being erroneously associated with you. If you prefer to use your real name, use only one (if you have more than one) with your surname, or use whatever combination of names you like in the first and surname fields. Add a subsequent name initial if you need to distance just a bit from someone else with your name ;) If you don't feel comfortable using your real name on the internet, don't use your real name on the internet.
- partials/nicknames and initials: if you want to use your real name but don't feel comfortable using the lot, you'll stand out less if you use part of your name or initials. I am usually mononymous "bek" where I can get away with it on sites with "real name" policies, though I used my initials "dc" in the surname field of G+ in the early days to avoid their overeager banhammer scripts that seemed to think mononyms weren't "real", and then never bothered changing it. Sensible places will let you get away with a mononym if you put a space, - or . in the surname field if they require the surname field. Alternately use "Just" for the first name and your first name as the surname.
- pseudonym/handle: the ones that people recognise as Not a Real Name are immediately recognisable as pseudonyms. Names that are recognised as real names might also be pseudonyms, because you don't know for sure it's the person's "real" name (unlesss you know the person). Go with as real sounding or as ridiculously outrageous as you like, it's your nym and you have to live with it :) If you're going pseudonymous on a site that has "real name" policies (particularly looking at G+ and Facebook here), go with something English-sounding. They occasionally struggle with the concept of non-English names. Actually they really struggle with the concept of pseudonyms, pseudonymity and privacy in general, so it would actually be better just to avoid them altogether.
- whatever kind of identity you choose, for integrity and recognition use the same handle/email combo wherever you sign up an account (emails are not usually shown unless you choose to show them but some sites will allow site members who have your email address to search that site to see if you have an account there). For privacy/low level anonymity (perhaps you're a mummy blogger who also writes BDSM) use different handle/email combos in the appropriate areas. The anonymity you gain from this is low level because while you might easily prevent your casual internet using family and friends from inadvertantly stumbling over your secret fetishes this way, anyone determined enough to prove that your two (or more) identities were the same person could do so without major difficulty unless you level 5 and drastically change your online habits to maximise anonymity. As long as you're not sock puppeteering or trolling, people generally won't bother.
- passwords:
- "everywhere" pushes using at least mixed case and numbers and strongly suggest also using special characters. I recommend using a short sentence fragment or mnemonic device that is easy for you to remember, not easy for other people to guess and include numbers and punctuation if you can. Some sites won't let you use spaces in the password. If you're using a sentence fragment either run it together so there are no spaces or use dashes for spaces (which then also count as special characters). e.g. you could use "Sassy is a cute cat!" for a password which gives you mixed case and special characters. Remove the spaces (Sassyisacutecat!) or replace with dashes (Sassy-is-a-cute-cat!) for sites that don't do spaces. You can l33t-5p34k and/or lolspeak if you want to complicate your passwords a little more and possibly forget them if you're not fluent in either (S4ss3h iZ t3h cUt3 kitt3h!). You can l33t dictionary words and use them as low level passwords, just be aware that good dictionary attacks will try more common l33t variations.
- basic security: have 3-4 distinctly different passwords in a tier system for everything. It's easy to remember and as long as your passwords are reasonably strong, it's safe enough for normal use. Use one password for things that won't be earth shattering if it's compromised, like forum accounts. Use another stronger password for sites that could compromise other people if it gets hacked (Facebook etc), a stronger one again for things that are important (email, anything that has your credit card number, net banking), and a really superstrong one for anything that has your credit card number and net banking if you don't want them to have the same password as your email.
- proper security: have a different password for everything.
- it's perfectly fine to use the same email address to sign up for different services. Just don't link those services. If you want to link accounts for convenience, using two-factor authentication (that thing where G+ or Facebook or your financial institute want your mobile phone number and occasionally when you log in or want to do something important like change account information or transfer money they send a verification code to your mobile to make sure you're the one making those requests) might increase your security a little but will reduce your privacy (you are giving them another thing to sell, and letting each service know what other services you use). If you use OpenID make sure your password is superstrong (but not the same as financial institute/anything that has your credit card number ones) and that you have a lot of faith in your OpenID provider.
- actually read the privacy policies and terms of service of anywhere you want to sign up an account. I know some of them are stupidly unnecessarily long winded and headache-inducing, it's done deliberately to make you scroll to the bottom without reading and click "Accept" and makes it harder to complain when they do something you don't like that you actually gave them permission to do. Checking them periodically for changes is also a good idea if you can find the time or the inclination.
- when on social networking sites with privacy controls, check your privacy settings after every upgrade, more often if you remember to. Sometimes they have a bad habit of "inadvertantly" changing.
- most social networking sites allow you to make groups (lists, circles, whatever) of your contacts. Use them for things you don't want to post publicly or that you only want to share with certain people. Be aware that it may end up getting leaked anyway so be careful what you post.
- when on social networking sites that have privacy controls, check your sharebox at the beginning and end of your post to make sure you're sharing with who you want to share with.
- a lot of websites make good money from data mining. If it bothers you, be careful with what you give them (where "give" is pretty much anything and everything you add to your profile, post and click on, including the "add as friend" type buttons and the "like/tweet/pin/+1/etc" buttons anywhere on the internet). If you don't trust the people who own the social network you're using (and you generally shouldn't trust them fully if they are a corporation), do not for any reason put home addresses, private/home phone numbers etc on social networking sites even if they helpfully give you a space to do so and encourage you "to make it easier for your friends to find you" (which it will, and you are also giving the service more data to sell, and they will). Different matter if you're on a friend/family member's Friendica/Diaspora/etc pod, in which case one would hope they are worth your trust if you trust them with that information. Friendica is also pretty good in that it allows you to have multiple profiles so you could conceivably display one profile containing your address and phone number only to trusted family and friends and present different ones to other people.
- remember that once something (from the fanart you post to deviantART to the cute photo of your kids running through the sprinklers on Facebook to your status updates or blog posts or comments on even "limited" posts) is up on teh interwebz, it can be nigh on impossible to get it off again.
- when sharing with a limited audience, be explicit if you don't want the post reshared past the people you share it with, and make sure you trust the people in that group/list/ircle to honour your wishes. If you're really worried about it getting out further, don't share it on the internet. Or at all. Likewise if someone shares something within a group that you happen to be part of, don't reshare it unless they okay it.
- if you feel like a bit of unscientific experimentation, install Collusion, open it up and keep doing what you do, and see what comes up on the thing before and after getting to your desired paranoia level. If you hang onto it after it's a nice visual for how your privacy/security settings are.
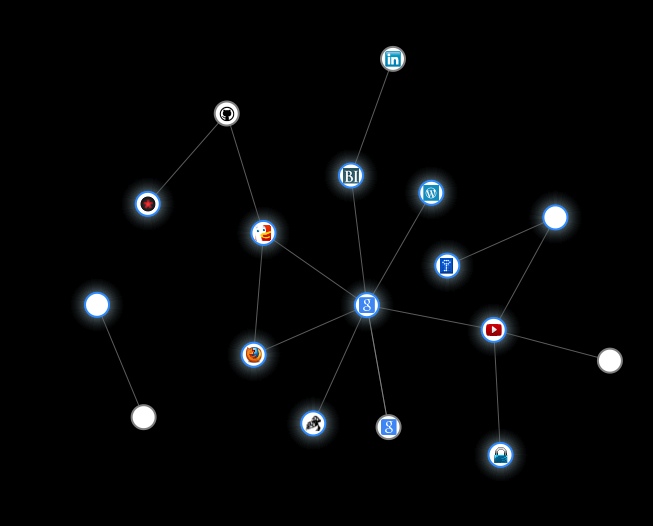
The image above is a screencap of my Collusion graph after scouting about for stuff for this blog post. During normal use it's a lot smaller than that. Glowy things are sites I visited, non-glowy things are sites that were informed that I visited the sites I visited. Would have been a bit more extensive if I didn't have a fortified browser. That middle "g" circle that almost everything is attached to is Google. I only used it directly once.
Level 2 - basic system and browser fortification
System
- keep your operating system up to date. Most of them self check and even offer to self update, so no real excuse :)
- require a login for your computer, even if there's only one user account on it and you are (theoretically) the only one that uses it.
- OSX: System Preferences, Users & Groups (in the System section which is the second last section unless you just unboxed the computer in which case it's probably the last section), unlock the pane if it's locked, click "Login options" at the bottom of the list of user accounts.
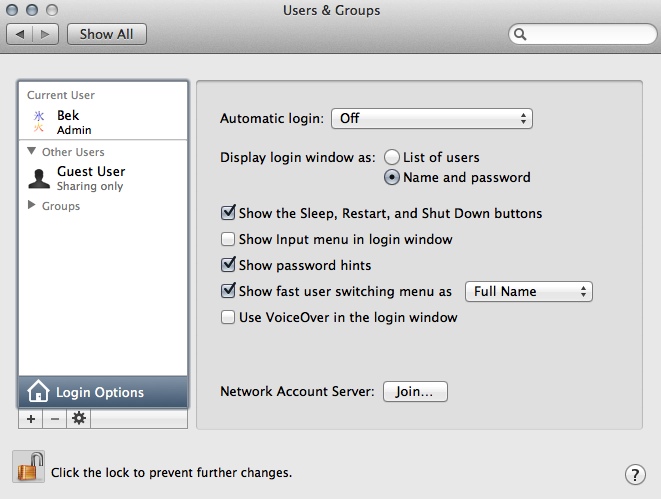
Set "Automatic login" to "Off", set "Display login window as:" to "name and password", do whatever you like with the checkboxes. If you don't have a password on your account, click on your account, select the "Password" tab if it's not already selected, and press the "Change password..." button (it may or may not say "Set password" if you don't have a password, I've always had passwords so don't know). Set/change your password. Don't make it too easy.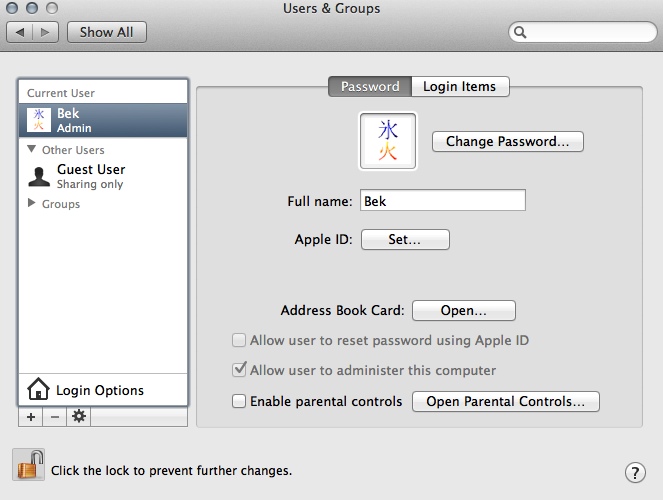
If your computer is a desktop, don't stress about the AppleID stuff. If the computer is a laptop, set the AppleID and allow a password reset from the AppleID if it gives you peace of mind in the event someone borrows your laptop and forgets to return it. It may be safer to leave it off if you like linking accounts and have any linked to your AppleID as if that gets compromised the compromiser can reset your password (among other things). - Win7: Start menu, Control Panel, User Accounts, Change your Windows password. There may be an option to set your password if you don't have one. It's been a long time since I've used Windows on an actual machine so I don't remember. I can't for the life of me figure out how to turn autologin off but I've never been able to do much easily on Windows. Quick search seems to indicate it's off by default and you have to jump through hoops to turn it on, but it would be very easy for me to be wrong there.
- Ubuntu: cog in the top right hand corner, "System settings" (or if you haven't modified your Launcher which is the thing down the left side that looks kind of like OSX's dock, it's the second last icon), you may have to unlock the panel.
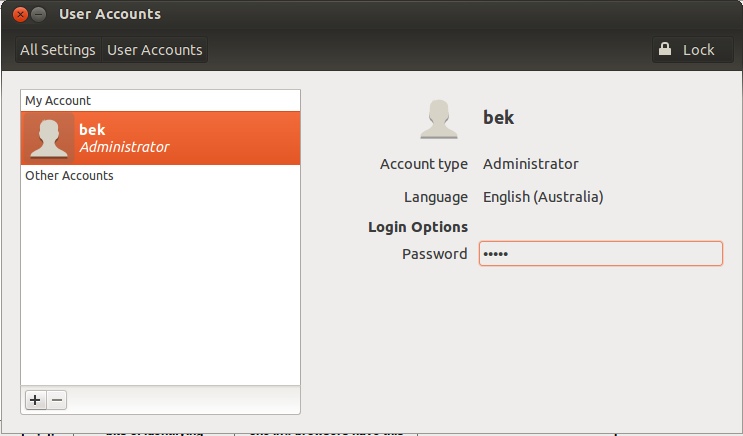
All the stuff there is clickable, click on the password box (can't really see it on my vm, not sure if it's always like that) and you'll be taken to a screen where you can set the password. (note: if you came back to top from following my very slight modifications to the Ubuntu install, you would have already done this during install) - set your screen to lock after a certain amount of time. It's in the "General" tab of the "Security and Privacy" pane on OSX, tick "Require password for sleep and screen saver" and select your time from the dropdown menu. On Win7, right click your desktop, click "Personalize", click "screen saver", check on "On resume, display logon screen" and set your time. In Ubuntu, it's in "System settings", click "Brightness and Lock" in the "Personal" section. Use the dropdowns to set whatever you want and slide the lock to "on" if it's off. Letting it lock after the screen turns off works.
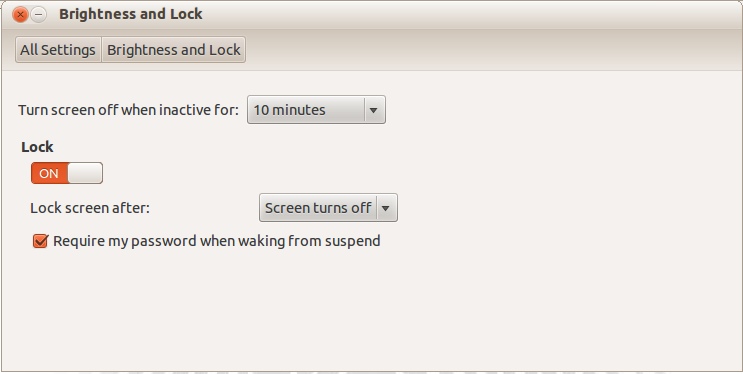
Again if you followed the slightly modified Ubuntu installation instructions you may have already done this. If you're confused as to why the colour scheme of this image is different from the previous one, I changed Ubuntu's theme while editing the guide.
- OSX: System Preferences, Users & Groups (in the System section which is the second last section unless you just unboxed the computer in which case it's probably the last section), unlock the pane if it's locked, click "Login options" at the bottom of the list of user accounts.
- disable the guest account if you don't use it. Ubuntu has a "guest session" rather than a guest account which can be disabled if you feel like doing a bit of commandline (it's not as hard or as scary as it sounds ;).
- turn off location services on your computer and any websites you use (allow specific websites and apps if it's actually useful for them to know roughly where you are). Decide if you want to help out the developers of your operating system by sending them "anonymous usage statistics"/"performance data"/etc. It does help them and most will do their best to anonymise and aggregate the data to make it really hard to track back to you, but it can happen. If you prefer definite privacy, opt out.
- optionally: if you want to be informed of when sites try to set Flash cookies, find your Flash settings ("Other" section in the System Preferences on OSX, you may have to visit the Flash settings manager on the Adobe site for Win7 and Ubuntu), go to the "Storage" tab/link and select "Ask me before allowing new sites to save information on this computer".
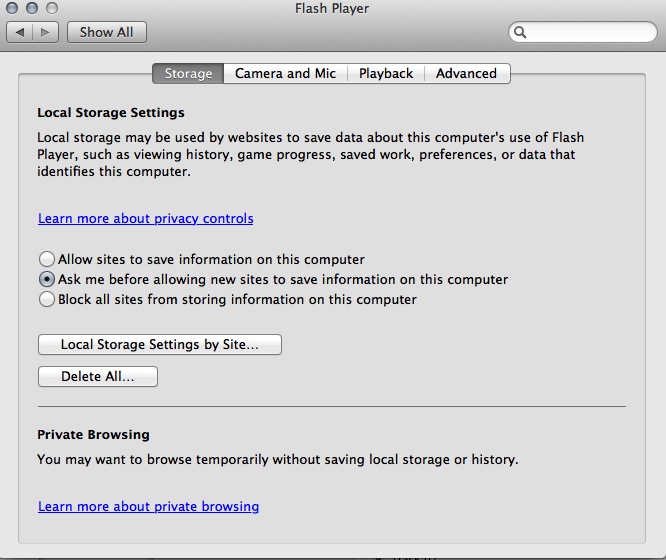
Next time you visit a site that wants to use the Flash player, you will be presented with this dialogue within the Flash player: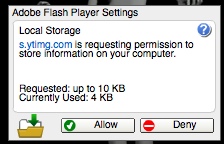
It may take a couple of clicks for the thing to go away. If you're playing a game (kids are using Reading Eggs, Moshi Monsters, etc), click "Allow", otherwise "Deny". Check the settings in the other tabs/links if you like, the most important things to check are to make sure that sites have to ask before they're allowed to use the camera and the microphone or use peer assisted networking (both should be set to ask by default). Later on we're going to be installing a Firefox add-on that will manage the Flash cookies so if the thought of having to process these dialogues every time you hit a site with Flash on it is unappealing, leave it at the default "Allow sites to save information to this computer" and use the extension to manage the cookies. - if you haven't already, get Firefox. Ubuntu ships with a slightly modified Firefox and will update it to a new version if necessary for you on install (if you have an internet connection and allow it to install updates which is a good idea). If you're switching browsers, import your bookmarks (optional but figured it might be convenient ;) and set the new one as your default. Flush the cookies, caches, history, and stored passwords and forms in the old one (to get rid of persistant cookies). Optionally bury your old browser (especially if it's IE).
- optionally (mandatory if you're on Windows or don't use a router to connect to the internet), if your computer has a firewall, turn it on. In OSX it's in the Security and Privacy pane in the System Preferences. In Win7 it's Control Panel, System and Security, Windows Firewall. Ubuntu's is on by default. The firewall defaults are fine for most cases. If you do more than email and travel the internet you may need to poke a few more holes in yours.
Browser
Firefox extensions can be sought, added and deleted using the Add-on manager (shift+cmd/ctrl+A in the browser, otherwise it's in the Tools menu), I'm going to use links to the Mozilla add-ons to make life slightly easier for the purpose of this exercise. They should require little to no configuration, and will pop up screens if they need initial configuration. The defaults should work in most cases, but don't be afraid to poke the preferences panels and have a look around. One of the first questions Firefox asks is if you want to help them out by sending anonymous usage statistics. Answer as you like. If you change your mind, the setting is called "Submit performance data" and it's right at the bottom of the "General" tab of the "Advanced" pane in the preferences.
- open the Add-on manager, click on Plugins, and disable Java (this plugin is conveniently absent in Ubuntu).
- open the preferences (cmd+, or in the application name menu on a Mac, under Edit -> Preferences otherwise)
- in the "Content" pane, tick "Block popup windows". You'll get a warning if a site tries to pop a window up and can choose if you want to allow it through or not.
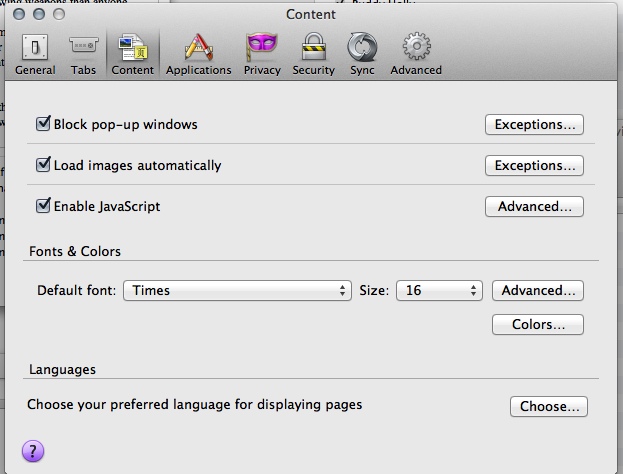
- in the "Privacy" pane, tick "Tell websites I do not want to be tracked", change "Firefox will" to "use custom settings for history" to display the list of checkboxes under that, and uncheck "Accept third party cookies". This may cause personalisation services to stop working which may cause problems if you use services like Amazon a lot. Take your pick between convenience and privacy.
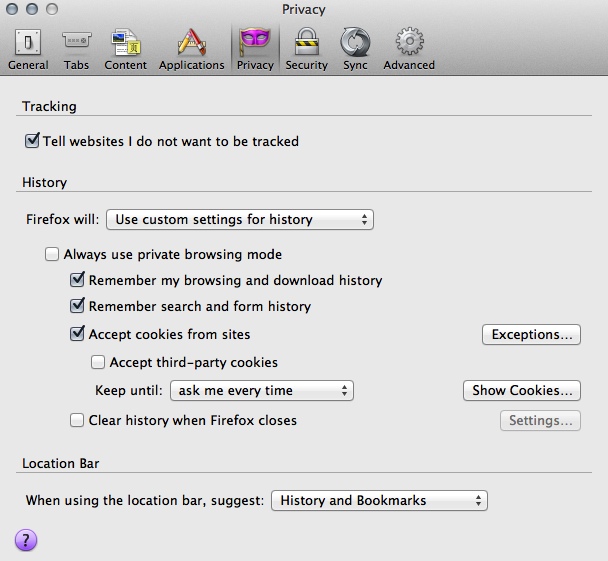
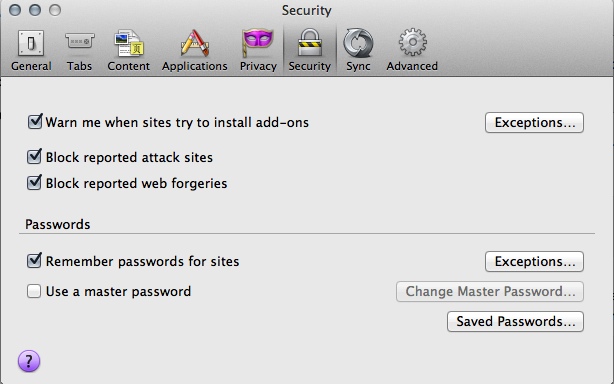
The other stuff is a matter of convenience vs paranoia. If you don't accept cookies at all, anything you log into will stop working properly (sites that are just setting tracking cookies won't be affected), and your login details and preferences won't be remembered. The settings I have in the figure will pop up a prompt every time a site wants to set a cookie (and a million times if the site sets lots of cookies). I will usually "Allow" base domains I log into and trust, "Allow for session" (which means it removes the cookie after you quit Firefox) if there is a legitimate reason for the cookie to be set (e.g. on sites like Artician and deviantART, the artist profiles are subdomains, and the cookies ensure you stay logged in across the subdomains) and "Deny" everything else. To not be hassled by the prompts every time you click on a link, set "Keep until" to "I close Firefox" for privacy or "they expire" for convenience. Be aware if you take the latter option that some cookies don't expire for years. If you find that some cookies you deleted have mysteriously come back without you having visited the site that planted them, you may have zombie cookies on your hands. An extension we're installing soon will take care of them. - in the "Security" pane, make sure "Warn me when sites try to install add-ons", "Block reported attack sites" and "Block reported web forgeries" are enabled. Decide whether you want to remember passwords for sites and use a master password, again this is a decision between convenience and paranoia.
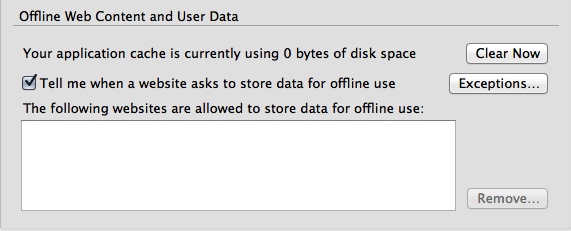
- go to the "Advanced" pane, click the "Network" tab and check "Tell me when a website asks to store data for offline use". Underneath there is a textbox. If it's not empty, remove everything in it unless you play browser based games, in which case delete everything that isn't from a game site as they'll be doing very little other than tracking.
- install the following (all but the last one will require a browser restart, you don't need to restart until after you've put them all in):
- NoScript: somewhat aggressive protection against clickjacking, cross site scripting and Java and javascript exploits. It will disable share buttons, Java and Flash and will absolutely mangle sites that use javascript for layout and various elements and anything that uses external comment systems such as Disqus and IntenseDebate, so if you frequently visit and trust a website that is getting mangled, permanently allow it. If you're not sure but need it to look legible or do something that requires some script, temporarily allow it. "Temporarily" means all permissions get revoked when you quit your browser.
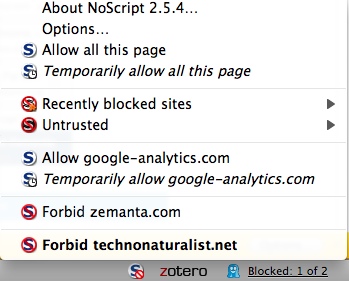
Most sites will be fine after you've allowed at least the base domain (if you want it to be slightly easier and slightly less secure, there is a thing in the NoScript options to automatically temporarily allow scripts from the base domain), some larger sites may require you to also allow their cdn. Flash videos will end up looking like this on blocked domains:
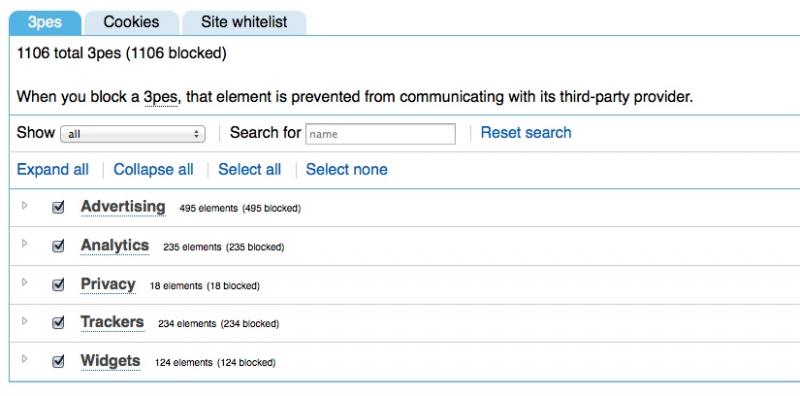
Other smaller elements may have a smaller version of the NoScript logo on top, click on them and okay in the NoScript prompt that pops up to allow just the element/s you want without allowing the whole site. You will get some websites that are borked even after you've allowed everything. My preference is to avoid them and any site that wants too many scripts enabled before it will look and function some semblance of normal, others would rather risk the tracking cookies/potential malware/etc and have less hassle. Again, matter of preference. You may notice pages loading faster now that they're not also loading a hundred million things from other sites. - Ghostery: fairly non-invasive. Has a cute little Pacman ghost-style icon (you can see it in the above image next to the NoScript icon). It wants initial configuration which is fairly easy, just click "Select all" in both the "3pes" and "Cookies" tabs, then press the giant right arrow to finish up.
Same as with NoScript, you may occasionally see some elements (notably social networking share buttons) blocked with the little ghost logo over it, You can click to enable them if you want to use them. If you're feeling charitable allow the analytics cookies through (or at least any from Piwik which is what I'll be switching to soon). I'm sorry for the fact that marketers go out of their way to use it to monetise sometimes at the expense of users, but it does help us webmonkeys out some as well :)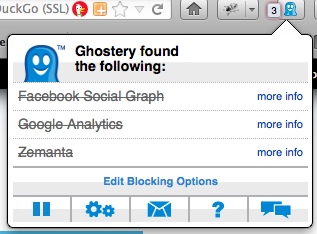
To allow some things through (eg if you want to pin or +1 or share on Facebook or participate in Disqus and IntenseDebate conversations) and leave out the rest, and block new ones that crop up and aren't blocked automatically, click the little ghost icon either in the add-on bar down the bottom of the browser or near the address bar at the top, click "Edit Blocking Options", uncheck the ones you don't want blocked and check everything else, then click anywhere outside of the bubble. Every time you visit a page you will get a purple notification bubble in the top right corner that will tell you what trackers it has found. It will block ones it recognises (shown by a strikethrough) but allow new ones through (they will be white with no strikethrough), and you can manually block them. Click on the bubble to make it go away immediately, otherwise it fades out by itself eventually. Opt-in to Ghostrank to report new trackers they may not have in their database yet.
Every time you visit a page you will get a purple notification bubble in the top right corner that will tell you what trackers it has found. It will block ones it recognises (shown by a strikethrough) but allow new ones through (they will be white with no strikethrough), and you can manually block them. Click on the bubble to make it go away immediately, otherwise it fades out by itself eventually. Opt-in to Ghostrank to report new trackers they may not have in their database yet. - BetterPrivacy: manage Flash cookies. Its defaults should be fine for most cases, if you want to configure it you have to do it after the browser has restarted as it looks for where the Flash cookies are stored while the browser is shutting down and then does its thing when the browser restarts, so the first time you restart after installing the add-ons might take longer than usual. Open it up by going to Tools -> BetterPrivacy. The first screen you'll see is this:
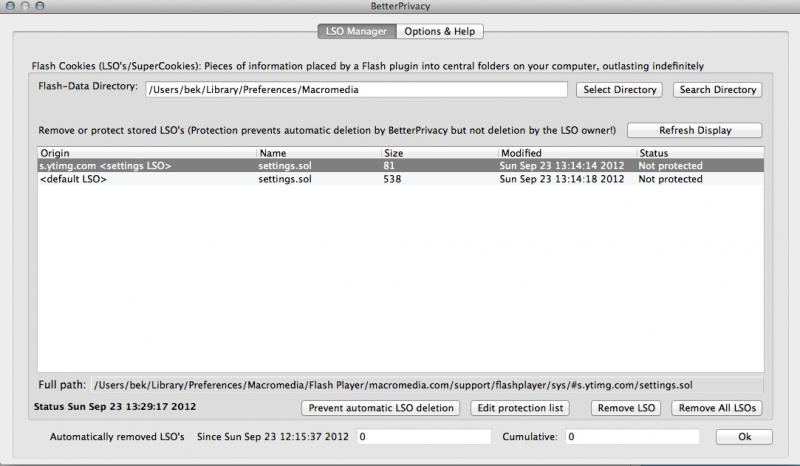
You want to keep <default LSO> which is your Flash player settings. This one will not be deleted unless you manually delete it or explicitly tell BetterPrivacy to delete it. If you recognise any urls as games etc that you play or sites that you trust, you can double click the "Status" of that cookie to change it from "Not protected" to "Protected". This will prevent those particular cookies from automatically being deleted when Firefox quits (the default behaviour) or when you press the "Remove All LSOs" button (which you may want to do if you happen to have a lot of them that you don't recognise/trust). It's also a good option if you don't want Firefox to always ask if you want to delete the cookies whenever you quit and untick the "Always ask" in the "Options & Help" tab. If you're feeling particularly paranoid you can tell Firefox to delete cookies at application startup as well as on quit, also in "Options & Help". - HTTPS Everywhere: https helps ensure the server/website you're communicating with is actually the server/website you think you're communicating with, and encrypts communication between you and them. If the website/server is capable of https, requests are rewritten so everything is served in https and thus encrypted and authenticated and you can be reasonably certain of not getting man-in-the-middled. Opt in to SSL Observatory to help detect forged certificates and to get warnings of potential browser attacks.
- Adblock Plus: set and forget. The internet is a much nicer place with no ads.
- NoScript: somewhat aggressive protection against clickjacking, cross site scripting and Java and javascript exploits. It will disable share buttons, Java and Flash and will absolutely mangle sites that use javascript for layout and various elements and anything that uses external comment systems such as Disqus and IntenseDebate, so if you frequently visit and trust a website that is getting mangled, permanently allow it. If you're not sure but need it to look legible or do something that requires some script, temporarily allow it. "Temporarily" means all permissions get revoked when you quit your browser.
- optionally install Convergence. It's an open source distributed replacement for the Certificate Authority system and usually works with/complements it. Rather than relying on a central authority to decree that certificates are valid, your browser checks certificates with notaries and if conditions that you specify are met (by default it's something like check with at least three and if the majority agrees the certificate is valid) then trust the ceritficate. Anyone can become a notary by installing the notary bundle on their server, and you can choose which notaries you trust. At time of writing it does cause some sites to render strangely and crashes the browser on others.
- there are a plethora of add-ons and themes for Firefox that you can have fun with if you like. Keep in mind some of the add-ons might not be the best for privacy/security (basically any kind of "toolbar" and anything that lets you share stuff on social networks with the press of a button), and don't get carried away, too many cause your memory usage to blow out and slow the browser right down.
- all this stuff is free so if you appreciate their efforts, please make donations to any/all/at least one of the projects.
So I've currently been running under the assumption that you already have and use an antivirus. You know what "they" say about assumptions. If you don't already have an antivirus program, use that shiny new fortified browser to download Sophos or ClamXAV (Mac), AVG (Windows) or ClamAV (Linux, there are ports but not sure of reliability) and install (and you'll get to practise NoScript on fairly trustworthy sites and have Ghostery show you all the trackers you could have picked up if you hadn't fortified :).
Ubuntu people can get ClamAV from the Ubuntu Software Centre (second last icon if you haven't changed your Launcher, otherwise click on the Dash which is the first icon and start typing "software"). If you're familiar with the Apple Appstore or the Android Marketplace/Google Play Store, the Ubuntu Software Centre is pretty much the same. Search for "clamav", install the "Anti-virus utility for Unix - base package", the "Anti-virus utility for Unix - scanner daemon" and "ClamTK" (so you can see what it's doing and get it to do things).
None of them should require too much configuration, though ClamTK might give you some scary warnings about being out of date (don't worry too much about it, the package manager should catch up eventually, though you can visit the ClamAV and ClamTK websites for updates if you don't want to wait). Do a full system scan (it may take a while depending on how big your hard drives are and how many of them you have, you should be able to continue using your computer if you want while the scan is in progress, or at least you can with Sophos). After the first one it's advisable to do a full scan every so often but they should automatically check all incoming files (sent to you over email or downloaded from interwebz) and give you the option to scan individual files (somewhere in the right click menu, in OSX it might be hidden in the "Services" submenu).
Do not turn them off, especially if something that you downloaded from the internet tells you to so it can install (this includes you, Flash). Sorry for repeating myself, I'd probably be rich if I'd charged for the amount of times I've had to fix computers that had problems because their users turned off the antivirus because a program they desperately wanted to install told them to turn off their antivirus so that it could (and then of course turned out to contain malware).
Level 3 - instant messaging, file and email encryption
Public key cryptopgraphy
Extremely basically, you have a key pair, consisting of one public key and one private key. As the names suggest, you keep the private key secret and give out the public key to whomever you want to communicate with. The file/email is encrypted with the public key of the person/people you want to send it to, and can only be decrypted by that person's private key. So if you want to send me something privately/securely, you would use my public key to encrypt it, and then I'm the only one who can decrypt it as I'm the only one with the corresponding private key. Anyone who's trying to intercept our email for whatever reason will not be able to read it/look at the file/etc as they don't have the right private key with which to decrypt it. You just need to make sure you have the right public key for the right person.
To increase trustworthiness you can sign the public keys of people you know/like/trust/all of the above (you can even set an expiry date on your signature if you like). Then if you get contacted by someone you don't know and you can see someone you trust has signed their public key, it gives you a pretty good idea that they're probably who they say they are and not a spammer or a scammer.
If you don't have someone's public key and want to assure them that you are actually you and not some idiot pretending to be you, the private key can be used to generate a digital signature that only you would have because (theoretically) you are the only one with access to your private key, which you can sign your emails with.
Instant messaging services
- download and install Adium (OSX) or Pidgin (Windows|Linux, available in Ubuntu Software Centre). These are basically the same program as Adium is the OSX version of Pidgin (there is also an OSX port of Pidgin, but they recommend you use Adium) and are multi-protocol clients which means that you are able to connect to multiple servives (MSN Messenger, GTalk, Facebook chat irc, Jabber, icq, AIM, etc), and very helpfully contain built in encryption and proxy ability per service.
- add an account (or several) using the + button at the bottom of the "Accounts" pane, enter any credentials if you need to, and poke around in the "Personal" and "Options" tab if you like. We will come back to the last two tabs.
- back in the main preferences panel, click on "Advanced", select "Encryption", select the account you want to encrypt and press the "Generate" button. A rather long alphanumeric fingerprint will be generated for you and the button will then change to "Regenerate".
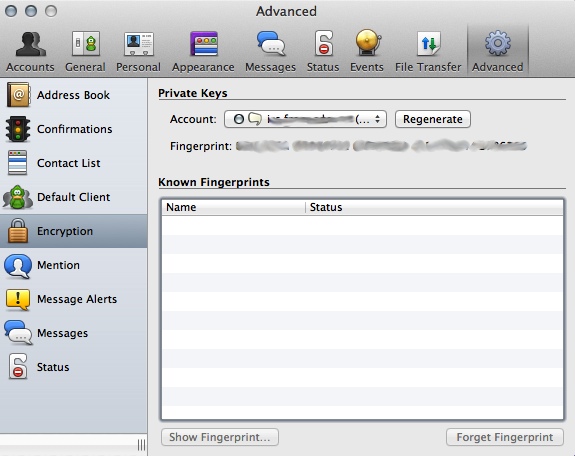
The "Known fingerprints" box is to collect public keys of people you have encrypted conversations with. If you don't have someone's public key fingerprint, you will not be able to encrypt your communication with them. - go to the "Privacy" tab, change "Encryption" to either "Encrypt chats as requested" or "Encrypt chats automatically". The last option may prevent you from communicating with people who haven't got the encryption stuff set up (don't know for sure, never tested).
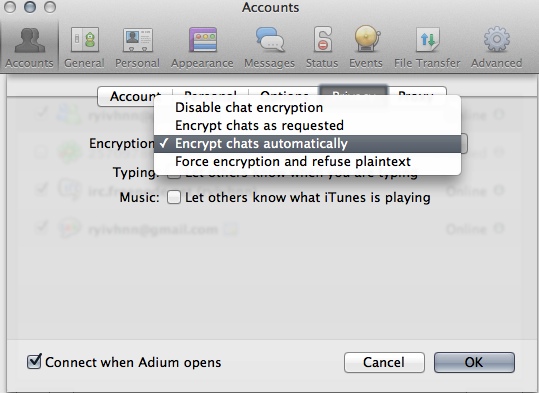
Untick the boxes below the "Encryption" dropdown.
Files and emails
Download and install GPGTools (MacOSX) or Gpg4Win (Windows). The GNU Privacy Guard (of which the former two are ports of) seems to be installed by default on most Linux distros and is already up and running in Ubuntu. You can use Seahorse (search for it in Dash) to generate and manage your keys. GPGTools is very easy to get up and running, it automatically sets up its plugin for Mail and puts itself into the right click menus (under "Services" on a Mac) so you can right click to encrypt and decrypt files. The website has a lot of documentation that is very easy to read.
DO NOT UNDER ANY CIRCUMSTANCES FORGET THE PASSPHRASE OR YOU ARE UP SHIT CREEK WITHOUT A PADDLE. Make a revocation certificate and keep it somewhere safe just in case.
If you're on Ubuntu, Thunderbird is installed and set as the default mail client. Use the Ubuntu Software Centre to find and download Enigmail which will give you signing and encryption. If you're on Windows and GPG4Win doesn't integrate with your mail client automatically, you may also want to consider Thunderbird and Enigmail as Enigmail seems quite capable of setting itself up.
There are apparently webmail services that will do email encryption. Try a search for webmail with gpg encryption and see if there is anything that fickles your tancy, and review the crap out of their privacy policies and terms of service.
Another useful thing GPG does if you're particularly paranoid: some developers will sign the packages they distribute over the internet, and provide a sig file with has the extension .asc to optionally download along with the package. Download the two files to the same place (if the files come in a few versions e.g. 32bit and 64bit make sure you grab the right sig for the right version), double click on the .asc file to import the key into your keychain, then right click on the file you just downloaded, go to Services, and select OpenPGP: Verify signature of file. If the asc and the signature in the file match, a box will pop up saying who the package was signed by, probably with (undefined trust) unless you've defined a trust level for the key. IF they don't, it will spit an error (invalid or error or something to that effect) in which case you'll know not to open it or at the very least it's not who it claims to be from :)
Level 4 - Trustno1
The section heading is a serious misnomer but I couldn't resist using Mulder's crappy password. If you're going to be on the internet you are going to have to trust someone to some degree. It's a matter of how much you trust them.
Search engines
For a search engine that doesn't track or bubble you and helpfully tries to hook you up with https where available when you click through a search result, use DuckDuckGo. It's the primary search engine on mine and the kids' browsers. I may be slightly addicted to the !bang syntax (get on there and type !wiki internet privacy into the search box), which anonymises your search to a degree, but for me is just a hell of a lot more convenient than switching search engines (I also have a search engine for Wikipedia on my browser) or going to the website in question and then using their search bar (I do a few !drupal searches in my browser bar). When you go to their site there's a link in the bottom right corner that will let you add it to your browser. If you want harder core privacy and anonymity, Startpage records exactly nothing about you (including your ip!), gives you the option of using a url generator to remember your settings for that search engine which negates the need to use/set cookies, uses POST requests which means your search terms aren't leaked (and also means you can't share your actual search results as all results pages are ) and on some search results you have the option of viewing it through their proxy and thus remaining completely anonymous to that site as well as Startpage itself.
Both search engines utilise Google seeing as Google has done a sterling job of indexing the entirety of the internet. Google doesn't see you when you're using them. If you use DDG to search Google (use !g in front of your search terms), Google receives the search query from DDG, not from you, even though you obviously get the results on Google's results page.
The email thing is entirely dependant on how you feel about and use your email. Some people prefer their email (and sometimes all of their files) "in the cloud" and thus accessible from anywhere and everywhere on all their devices (hopefully just by you). Others prefer to download it to their computers and delete it off the mailserver after it's been downloaded so they're (probably) the only ones with a copy. As far as I'm concerned neither is more advantageous than the other, it's dependant on how you like to work.
Having your files and email living in the cloud means thieves/mysterious government agencies/your nemesis get nothing but cached copies of your data (or nothing at all if you can delete the cached copies fast enough) and you'll be back up and running in no time if your computer explodes or vanishes, but requires you to trust your provider will not be evil, capitulate immediately without informing you to requests from people with important looking badges or pieces of paper for all of your datas, be able to withstand black hats and script kiddies, not go out of business and/or shut down everything suddenly etc.
Having all your files and emails on your computer means that it will start taking up a lot of space, easily mitigated by getting bigger hard drives or external media to store it on. Computers and their associated parts do die eventually so you need to make sure to keep transferring them as the old media gets less reliable. You can be reasonably certain that you are the only one able to access and use your stuff, however you will lose everything if thieves/mysterious government agencies/your nemesis snaffles your computer.
In either case you can make things harder with encryption (see level 5), and you can save yourself the pain of losing everything by having a good backup system.
Slight tangent...backup systems
We have a NAS with three 2Tb hard drives set up in a RAID on which we keep stuff we want to access easily but don't necessarily want occupying that much space on our computers, and I use for weekly Time Machine backups (managed by TimeMachineEditor because I find Time Machine's defaults a bit over the top and using TME was easier than messing with TM's plist file). I keep stuff I consider particularly important on an encrypted partition of a usb stick which travels in my pocket when I'm out of the house (about as far as I'll trust offsite backup; keep it on your keyring or you may accidentally wash it, not that I've ever done that).
Easier options are backing up either the entire hard drive or just directories/files that are important to you (makes for smaller files but risk of missing something), encrypting the backup file and storing it on the cloud (fairly safe asuming reliable provider/s as good encryption algorithms are usually not worth the effort of cracking) or on a (optionally encrypted) usb stick/external hard drive in a bank vault or at a trusted friend/relative's. Back up and rotate regularly.
And back on track
Unless you're particularly paranoid there's no real need to abandon/delete your gmail/hotmail/yahoo/etc account. If you would prefer they weren't reading analysing the text in your email to target ads, download and then delete them. As with browsers, you're not tied to your operating system's default mail client if you don't like it. Find one you like and that does the job for you and run with it.
If you're happy with the cloud/IMAP setup, skip this section.
On your computer client:
- modern mail clients will have a walkthrough for setting up your account. They usually want the email address you're setting up collection for, your "Full name" (put in whatever you want to show up in the "From" field, it doesn't have to be your actual full name no matter what they say :), your username (which may be the email address, sometimes with + instead of @, not just your username) and your password
- next screen, if the client fails to autoconfigure, you'll be asked for incoming and outgoing (smtp) servers. You will need to check on the POP/IMAP settings page of your webmail client, they are usually mail.[your email service].[tld] or a slight variation thereof eg Gmail's POP server is pop.googlemail.com.
- If you didn't get asked during account creation and setup, go to the Advanced settings and if you can find an option to "Use SSL" or something similar, tick it for both incoming and outgoing. You may have to ensure you're using password authentication for outgoing. SSL is what is underneath HTTPS, it encrypts what is sent over the connection and makes it harder for people to snoop on you (and then combine it with encrypting your email in the previous level and you're generally pretty safe).
- set your client to delete email off the server after it's been downloaded. You may be able to set a timespan (immediately, 1 day, 1 week, 1 month etc). If you like checking your email from multiple devices, pick one of them to be the one that contains ALL OF THE EMAILS and have that one delete messages off the server, and only open that client once a day to download and delete all the messages. Make sure your devices don't delete emails off the server after downloading them. Because you are using POP rather than IMAP, you will have to delete the copy of the email on the device to save space on the device if you don't need the email.
On your webmail:
- disable IMAP
- if you're not using multiple devices to access your email, set it to delete messages after they've been accessed by POP (on the offchance it won't allow the client to do it).
Social networking
For extra security/privacy on Facebook/G+/etc:
- use a different browser only for social networking (e.g. use fortified Opera only for social networking and fortified Firefox for everything else, this stymies the trackers which now can't follow you all over the internet, I didn't suggest fortified Chrome which would probably be just as capable but if you're seriously contemplating this you probably don't trust Google either).
- have a dedicated email address only for social networking (or make one for each service if you want to be hardcore about it).
When I have some time and enough money for another Linode, I'm going to be starting up a Friendica pod. There are open Friendica pods about the place if you want to check it out in the forseeable future. Alternately there is Diaspora which is a better known distributed network also with a few public pods.
For paranoid blogger/blogspot bloggers, your biggest obstacle is going to be the amount of work it will take to export and re-import your existing blog somewhere else (if you don't want to start completely afresh), and potentially losing a few readers/subscribers who don't notice that you've moved. There's a hundred billion options if it's too cost prohibitive to roll your own. Look around. Otherwise there's shared hosting for any budget, it's a matter of finding one that you think you can trust (research and ask for recommendations) and then setting up Drupal or a self-hosted Wordpress or other cms of choice.
Level 5 - it's not paranoia if they really are out to get you...
On-the-fly encryption
With on-the-fly encryption, all your stuff is encrypted until you want to use it, at which point your computer decrypts it just before opening it, and then encrypts it again when you close it. You may notice a performance hit ranging from barely noticable to it's lagging heaps. This may cause problems if you work with large files such as those generated from video or sound editing, massive digital paintings or photos in RAW format.
First of all, decide what kind of encryption you want. This is important as it will determine the amount of preparation (mostly involving backing up all your stuff but some background reading is always advisable) you need to do, the amount of work that's going to go into it and the contingency plans you're going to make if something goes wrong. Please weigh up and decide BEFORE embarking on partition/volume/system level encryption as while permanently decrypting OSX is a simple matter of turning FileVault off, in can get tricky on Ubuntu and Win7 from what I've read.
- container: this is kind of like a folder on your hard drive, but requires your passphrase to get into. You can work on files and folders in here just as you would with normal files and folders. This is the easiest and least terrifying invasive option. Its drawbacks are you have to be careful to remain within the upper limit you set, or if you make a variable sized container that expands with the stuff you put in, be aware that TrueCrypt containers stay at the larger sizes it ends up at and you will not recover this space unless you delete the container.
- partition/volume: a designated area on your hard drive is encrypted, and anything in other partitions are not. With this and the above option, you need to be mindful that programs often spawn temporary files while you're working on something, and information may be pulled from these temporary files even after you've tucked whatever you were working on back into its encrypted container/partition or never moved it out in the first place. If you're working on particularly sensitive things (or are just overly paranoid), you either need to know where to clean up the temporary files or consider system level encryption.
- system partition/drive: your whole operating system is encrypted which means you need to authenticate or it won't boot at all.
- hidden volume: created inside a normal TrueCrypt volume, and requires another password to decrypt.
- hidden operating system: basically, you have a "decoy" operating system on top of a hidden volume which contains the hidden operating system. You would probably do all your clandestine stuff in the hidden operating system and normal activities in the "decoy" system (as having an unused decoy system looks suspicious). Not many would think to look for the hidden volume system or even be able to prove it's there if they suspect so it's something for people who live in evil regimes. I've also decided its paranoia level is off my chart so if you think something like this would be cool, do some reading of TrueCrypt's docs and have fun :)
It is entirely possible to have a setup where you have full disk encryption with encrypted partitions with encrypted containers in them (require three preferably different passwords to access whatever files are inside that encrypted container), expect a performance hit.
Full disk encryption is a good idea for laptops, and not a bad idea for external disks, usb sticks and other equally portable data carrying things to either be fully encrypted or have an encrypted partition or container on them depending on what kind of things you carry/store on them. On your desktop it depends on what kind of information you have on there and how paranoid you are that the desktop will sprout legs and go for a wander. The main drawbacks to full disk encryption are data corruption (most likely to happen if you randomly and unexpectedly lose power while it's in the process of encrypting or decrypting) or hardware failure (if it can't get to the bit where you can decrypt the drive, you're going to have problems). It will be inconvenient rather than tragic if you have backups :) Another option to consider if you're particularly paranoid or just in the market for some new hardware; hardware-based full disk encryption (aka "self-encrypting drives") which apparently perform a lot better and are supposed to be more secure as the keys and things are not stored with applications or in the operating system.
Now download TrueCrypt for your operating system. I'm going to be referring to the TrueCrypt docs and off-site tutorials a lot as I haven't attempted system level encryption on Windows or Linux. Each operating system version is pretty much the same bar a few features which I noticed were mising in OSX (where it also looks brutally ugly but technicalities) so even though the instructions are for Windows you can follow along in whatever you use.
Encrypted container
For all operating systems, TrueCrypt has an easy-to-follow tutorial on its site, though you could bungle your way through it by reading the prompts (ACTUALLY READ THEM, THEY ARE IMPORTANT) and clicking the "Next" button, and remembering that you must not give the container the same name as an existing file or you will destroy the file with that name.
Non-system partition/volume (can also be used for external drives and usb drives)
Before proceeding with partition/volume or system encryption on any operating system, it's strongly advisable to back up your system or at the very least files that that are important to you.
For Win7 and Ubuntu, the process isn't much different from creating an encrypted container, it just comes with scarier warnings and dialogues. In my example I'll be using screenshots from creating a TrueCrypt volume on my usb stick, which was initially formatted and partitioned using OSX's Disk Utility.
- click on the "Create Volume" button.
- select "Create a volume within a partition/drive", then next.
- select "Standard TrueCrypt volume", then next.
- press "Select Device". In the dialogue that pops up, choose your drive. I recommend labelling your drives to ensure you don't select the wrong one. In my case I am going to encrypt the partition called "backup" on my usb stick.
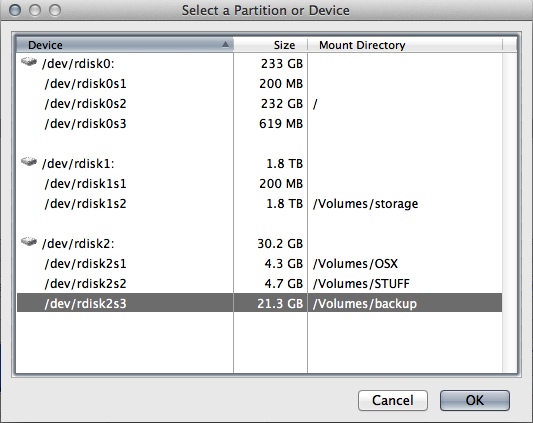
- press OK.
- back on the screen where you were, the textfield will be filled with the volume's device name. Make sure you have everything that was on the drive/partition (if anything) is backed up somewhere else, then press Next.
- Big Scary Warning will pop up strongly recommending inexperienced users create a container instead and asking if you're sure you want to encrypt the entire device/partition, and reminding you that files are going to be destroyed with this method. Click "Yes".
- a smaller scary warning will pop up telling you that formatting the device will destroy all data on that file system and ask if you're sure you want to continue. Check again just to make sure the stuff that was on the partition you're about to wipe is in fact safely backed up elsewhere, then click "Yes".
- next screen spits up Encryption Options. The defaults (using AES for the encryption algorithm and RIPEMD-160 for the hash algorithm) should be fine for most cases as it shouldn't have a huge impact in the performance of most machines (not sure if they're particularly old ones) and will present problems for normal government agencies (but maybe not mysterious ones).
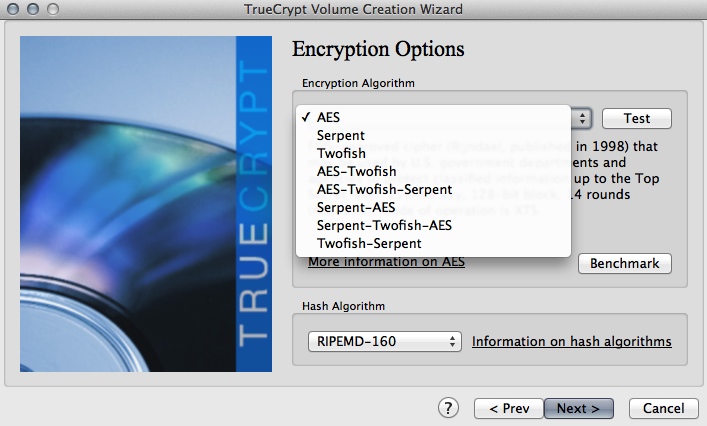
- now you do the volume password. Yep, you guessed it, DO NOT UNDER ANY CIRCUMSTANCES FORGET THE PASSWORD OR ALL THE STUFF IN THE ENCRYPTED VOLUME IS UNRECOVERABLE. The recommendation on the screen for a "good" password is 20+ characters of random mixed case letters, numbers and special characters and not to use names or birthdates. Again I recommend a short phrase or mnemonic device that is easy for you to remember and not so easy for other people to guess, mix the case and try to work special characters into it. Hell, write it (and all your other passwords) down and keep it somewhere safe, like in a safe.
- the next couple of questions helps TrueCrypt decide how it's going to format the volume. Answer them with whatever applies to how you're going to be using the drive.
- If the drive is new or has never had sensitive information on it, tick "Quick format". The next prompt to click through is one warning that if the drive had any sensitive data on it, it may be recoverable by disk recovery tools and some dedication. It will, however, make your format go quicker. Move your mouse randomly around the "Volume Format" window to increase the cryptographic strength of the encryption keys. Do it for as long as possible til you get bored, keep going for a bit more, then press "Format". You will get another scary warning reminding you that all files currently stored in the volume are going to be wiped, erased, lost, unrecoverable, so make damn sure that you have them somewhere not in that partition. Click "Yes" and let it do its thing. How long it takes will depend on how big the drive is and whether it's quick formatting or not. When it's done you should get a success prompt to OK. After that you're given the option to either encrypt another volume or exit.
- back at the main TrueCrypt window, your newly formatted device/partition/volume should be listed in textbox next to the blue TrueCrypt logo. Select any of the empty slots in large window of the numbers and click "Mount". You will be asked for the password that you set when you were creating the volume. Enter it and OK. If you'd labelled it before you will probably find that it lost its label during the reformat. You can rename it in the usual fashion now.
You will need TrueCrypt to be running if you want to mount and work with the encrypted partition. If you're wanting to access the encrypted partition on other computers, you will need to either have TrueCrypt in portable mode on the stick (I think it may be Windows only) or you will need a copy of TrueCrypt and admin access on each computer. To mount a non-system TrueCrypt volume:
- click "Select device".
- enter the admin password for the computer.
- a screen will pop up with all the devices you can mount. Select your TrueCrypt drive from the list, select an empty slot in the main window, and hit "Mount".
If you use OSX Lion+ and you're encrypting partitions on the same hard drive Lion is on or additional hard drives inside the computer, or you are quite, quite certain you will never, ever use your external hard drive or usb stick with anything other than a computer running OSX Lion+, you can use Disk Utility to encrypt the hard drive using the format MacOS (Journaled, Encrypted) rather than using TrueCrypt.
- hit cmd+space and start typing "disk utility" until it pops up. Select it and press enter. Alternately, it's in Applications -> Utilities -> Disk Utility.
- in Disk Utility, the disks with the hard drive type labels (e.g. 2Tb Hitcachi in the case of mine) are the actual disks, and the "subfolder" disks under them are partitions (e.g. storage on mine).
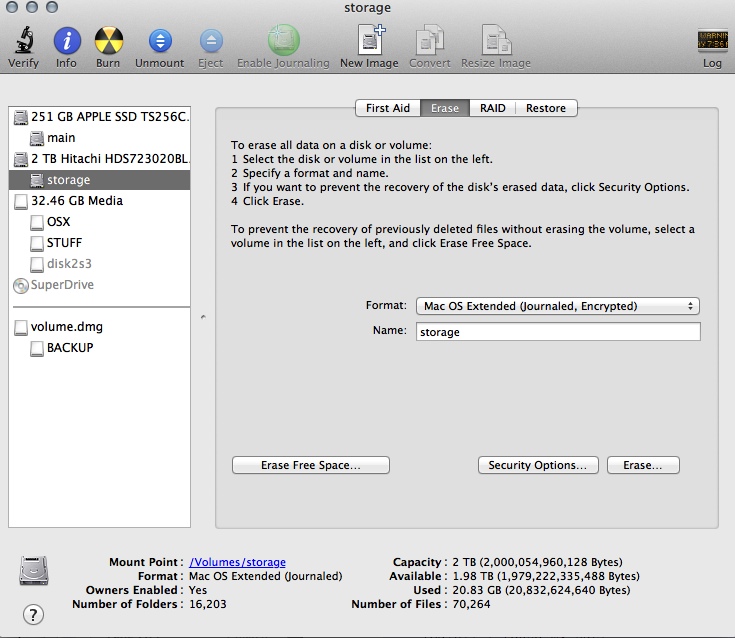
Two partitions you can't see in this utility but which showed up in TrueCrypt's browser and on command line tools are the Lion boot partition (650ish Mb) and some swap space (about 200Mb). My secondary drive also appears to have a 200Mb swap partition. If you want this space back or you're worried about the swap space not being encrypted (I think you specifically need to encrypt it in Ubuntu and Win7, OSX Lion+ FileVault theoretically also encrypts the swap), you can format the top level drive. I conceivably could as I have 16Gb of ram so probably don't need the swap that much, but I also have a 2Tb hdd so don't really care. If you're already feeling nervous, just select the partition (if there are no other partitions that one partition will be occupying the rest of the available space). - click on the "Erase" tab
- set the format to "MacOS Extended (Journaled, Encrypted)".
- optionally give the drive a descriptive name
- optionally hit the "Security Options" button and slide the slider up if the drive had sensitive data on it once (it will make the format take longer).
- hit "Erase". There will probably be scary warnings agin about making sure there's no data you want to keep on the drive as it will be obliterated and you will have to set a password. DO NOT FORGET THE PASSWORD. And don't you dare tune me out. Wait til it's done. The bigger the drive the longer the wait generally so you may need to leave it overnight. The Macs seem to be fairly good at recovering this type of thing but you may want to disable sleep/hibernate just while the formatting/encrypting is going on.
Next time you want to access your encrypted drive, you'll be asked for the password you set when you were formatting it. What don't you do?
Security advisory: anyone with access to your computer can access an encrypted partition while it's mounted. Either dismount it when you're done or make sure your screen locks after an idle period.
System partition/volume
Win7: this tutorial is a bit more step by step than the TrueCrypt documentation and has pretty pictures. Please be reminded I have never done this before :)
Ubuntu: a bit of an involved process, and again one I haven't had a chance to try out yet. This guide looks quite thorough, though it's for Xubuntu (which is Ubuntu with a different user interface). If it's looking too terrifying, just do the encrypted home folder. You'll be fine.
OSX:
- open System Preferences.
- go to the Security and Privacy panel, click on the Filevault tab, unlock the pane if necessary and click the button that says "Turn on FileVault".
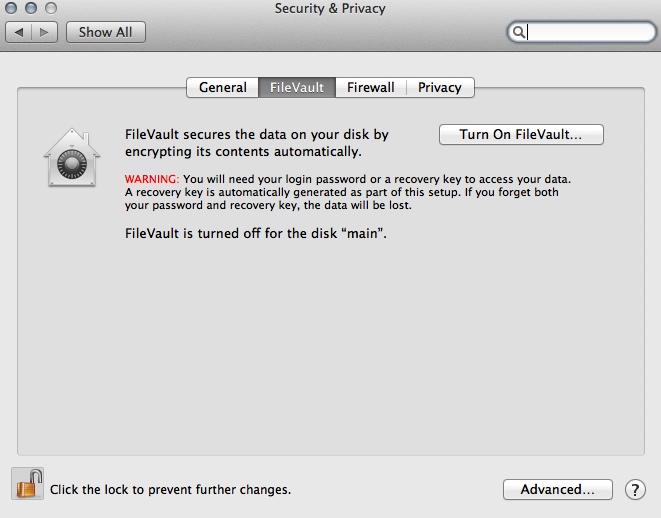
-
FileVault generates a recovery key and will pop it up onto another screen. Copy and paste it into a text document and save that somewhere safe (somewhere in one of your folders and then again onto a usb stick). On of the screens will ask if you want to send the recovery key to Apple. Some people prefer to do it in case they forget their password and then they can get Apple to possibly help them (they might not if you don't answer your security questions exactly right). Due to social engineering not being that hard I prefer to just not forget the password and keep the recovery key somewhere safe off the computer (keep it in the safe with your other passwords). You will not need this unless you forget your password so do not forget your password (or let your AppleID get hacked and reset your computer password for you). It will then do its thing and then want a restart. After you've rebooted it will begin the encryption process. You can continue to use your computer while this is going on.
DO NOT FORGET THE PASSPHRASE OR YOU WILL NOT BE ABLE TO ACCESS THE ENCRYPTED STUFF.
Basic obfuscation
Simplifying a lot, Tor works by bouncing you through a relay so your apparent ip doesn't match your actual ip, which makes it difficult for trackers etc on the website you requested and people trying to snoop on you to work out where you actually are. Because you're bouncing through relays your ip may change periodically, which may cause you to be logged out of anything you're logged into. I haven't experienced any noticable issues with instant messaging just yet (though to be fair I was only able to easily Torify the service I don't use often). Email takes slightly longer than usual to connect to the server to check for email (assuming you're using a client on your computer and not webmail) and browsing (which would include using webmail) takes longer when compared to non-Tor email and browsing. My last upgrade experiment with the Tor Browser Bundle indicates that it gets reset to a default when you upgrade the bundle, so if you want to use it as your normal browser you may have to keep exporting your bookmarks before upgrading and importing them after.
- browsing:
- download and install the Tor Browser Bundle for your operating system (available in the Ubuntu Software Centre). It should work out of the box.
- instant messaging:
- unless you need to keep logs to collect proof/evidence/testimonials/etc, open the Preferences, go to "General" and uncheck "Log messages" for privacy and plausible deniability (if there are no logs, it's very hard to prove the conversation happened).
- in Preferences on the "Accounts" pane, select the account you want to send through Tor, click the "Edit" button, click the "Proxy" tab, tick "Connect using proxy", change the "Type" to "SOCKS5", enter "127.0.0.1" (which is your computer) as the "Server" and "9050" as the "Port". Do this for all Adium/Pidgin services you want to go through Tor (the Proxy tab is the same for everything).
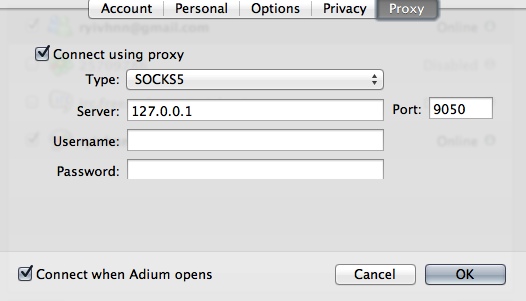
You may have trouble with irc if your exit node is banned by the server you're trying to connect to or the server disallows connections from proxies. Google tracks where you log in from and panics if you suddenly log in from somewhere different. If you log in to G+ and GTalk on Adium through Tor, it will probably just send you a notification letting you know you've logged in from a different ip and was it actually you and would you like to give them your mobile number for the much more secure two-factor authentication? While I was testing I managed to forget I was logged in to G+ on my unTorified browser and tested logging in to GTalk on Adium through Tor (which came through on a completely different ip). Google blocked my attempt to connect over Tor and sent me urgent "account possibly compromised" messages and asked if I recognised the activity. Imagine similar may happen with Facebook and other social networks that provide chat but don't have accounts to test. - if you're using Thunderbird for your email, download and install TorBirdy (at time of writing it will munge the Get Extensions page of the Add-on manager, so if you want more add-ons you will need to use the Mozilla add-on site).
Tending-towards-silly obfuscation
Use Tails. Alternately set up Virtualbox with a guest operating system different to the one you're currently using and browse from there with (takes a bit of stuffing around to get it working) or without Tor (at the very least you show up as a different OS). Or if you want to get really silly about it, you could try following the guide in the TrueCrypt docs to set up hidden operating systems or something like The Ultimate Guide for Anonymous and Secure Internet Usage. Seriously, unless you're living in an evil regime or someone is trying to kill you, this is probably more hassle than it's worth, and as I mentioned earlier, this paranoia level is off my chart :)
Tor isn't a magic thing that will suddenly make you invisible and anonymous because you're using TorBrowser. You have to do a lot of things to ensure no information that could reveal your identify is leaked, such as not using your real name or the real names of anyone you know, hoping that they remember to do likewise if they're in on the whole anonymity thing or make sure that they don't find out and accidentally out you. An option with this kind of setup is having two lots of apps/app profiles/accounts, one set for exclusive use with Tor when you're doing anything that requires extra discretion and the other for normal use.
Likewise disk encryption will only keep your stuff safe as an absolute last resort if the unthinkable happens and your computer is stolen. You should still take precautions to keep the machine itself safe, like not letting your laptop too far out of your sight when travelling with it. If you use full disk encryption, everything is only encrypted while you're logged out and/or the machine is off. If you're logged in, it's all decrypted, so make sure you either log out when you're done, or at least have the screen locking when you've been idle for a period.
Got linux?
Err...bek...didn't you say you use OSX?
Yah.
Why are you recommending Linux instead of OSX then?
I generally recommend whatever system is going to work for the person. I'm taking the opportunity to plug Linux simply because it's free and due to the way it's developed it tends to lack the questionable ethics and business practises that seems to plague "megacorps", and Ubuntu in particular is mostly brainless to set up so the "too geeky and scary" excuse doesn't apply. A number of my friends (and possibly other people) like "ethical" and probably wouldn't argue too hard with "free" or the idealistic philosophy behind open source. You wouldn't use Linux if you needed/were particularly attached to a program that didn't have a Linux version. My sister for example loves Photoshop and Flash. She does not like The Gimp. It doesn't matter that The Gimp can do pretty much everything Photoshop can do (some say more, but I have never hit full usage of either). She simply does not like it, therefore Linux is not an option. For me, it's Lightwave. If there was a Linux version of Lightwave, I could conceivably shift my rig without batting an eyelid (and probably would, everything else I use is free/open source and I love KDE4, though I would miss a billion little things in OSX, perhaps other people with programming ability will implement them). However, there isn't. There is Blender which is great and powerful and all that, but I don't get on with it, and it's not from lack of trying.
If you're not particularly attached to any particular program and anything that will do whatever it is you want to do will...do...seriously consider saving yourself $200 odd.
You can dual boot Ubuntu if you're too scared to blow everything away, and they even have a Windows installer if you're a Windows user and not ready to part with Windows yet. If you're ready to make the switch, make sure you've backed up everying important to you and follow the Ubuntu installation instructions. At their step 8, make sure "Require my password to log in" is selected and tick the "Encrypt my home folder" checkbox. That's it. And you thought it was going to be hard :P Now go back to the top and fortify it :)
Yes I can help/do it for you (if you're friends/family and local), I will need your computer for a few hours (how long depends on what paranoia level you want to go to and if you want me to install Linux for you). More if multiple accounts are required. More if any of those accounts require "management" (aka parental control).
No comments yet
- Reply